
Advanced Persistent Threat (APT) reduction
Don't make easy for hackers to learn from your log files
Advanced Persistent Threat (APT) attackers invest time and effort to learn your vulnerabilities - log files are too valuable to leave unprotected
APT and Log File Protection
Log files help APT attackers learn about your organization, your vulnerabilities and how best to evade your security measures.
Harden your defences against APT attacks by encrypting log files using Randtronics DPM easyCipher Transparent Data Encryption (TDE):
- easy to implement: no-code changes, fast install, minimal performance overhead
- standardized protection: centrally managed, policy-based protection Transparent Data Encryption (TDE) with centralized key management for protecting databases, servers at the file/folder level
- ‘air gap’ protection: security that can not be side-stepped by system admin or other privileged accounts
Why Now?
Advanced Persistent Threat attacks require sophisticated skills and the time and patience to spend extended periods of time gathering information from multiple targets.
This style of attack requires dedicated and resources but can yield substantial results both in terms of financial gain but also in terms of disruption.
For nation states that choose not to follow international norms, APT is an attractive form of asymmetric warfare that is easy to deny, and can deliver spectacular financial and disruption results for relatively small investment. With little downside and a strong payoff it is likely that APT attacks will to continue to mount.
Why Wait?
With Randtronics DPM enterprise encryption, it has never been easier to rollout and manage TDE encryption for all your databases, servers and laptops.
We envision a future where organizations standardize TDE protection all systems – no more second guessing as to whether the data might be useful to an attacker – no more gaps for APT attackers to exploit vulnerabilities.
Start today by adding log file protection to your current encryption initiatives for databases and servers:
i) Replace native database TDE with a security system that can protect everything on the DB server
ii) Protect secrets on web servers
iii) Protect content on file servers – including from system admin and other privileged users
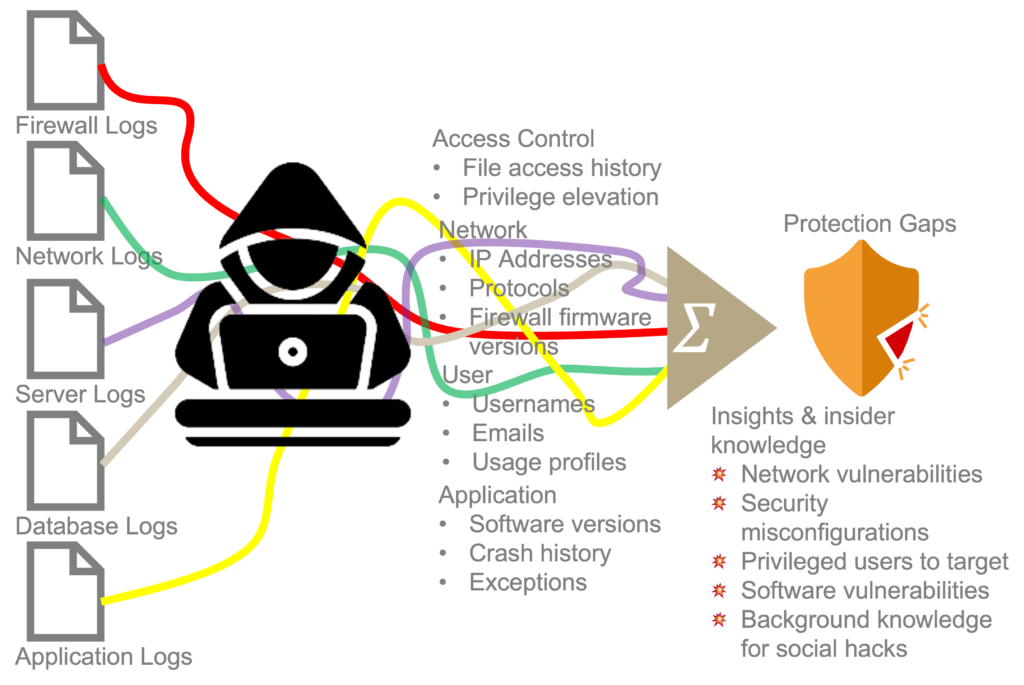
As a result of stricter audit and compliance requirements, it is increasing common for organisations to preserve many years of log files from networks, servers, firewalls, access control systems, applications and other systems.
To a diligent hacker who has managed to gain a toehold inside the firewall, log files contain troves of information that when pieced together can point to system vulnerabilities and/or provide background and context for customised and plausible social hacks.
Why TDE?
There are many types of encryption that address different types of risk.
Volume or full-disk encryption provides protection against physical theft as data can’t be read until user logs in. However, once a user has logged in, the data is now readable to anyone who can gain access.
Transparent Data Encryption (TDE) as provided by Randtronics DPM easyCipher secures the contents of files and folders when multiple users have access to the same systems. Moreover Randtronics TDE provides protection against data theft even by attackers that have gain access to system administrator privileges.
Randtronics DPM easyCipher
DPM easyCipher provides transparent data encryption for databases, web/app servers, file servers, NAS storage and end-devices.
Data policies and encryption keys are managed centrally providing enterprise-wide control of sensitive data.
DPM agent installed on end-point-device mediates all access to secured folders and prevents access from any non-whitelisted user or application.

Latest news and articles
Wide-ranging attacks against Barracuda appliances linked to China
This week the news broke that Mandiant (an incident response firm) attributed the recent cyberattack campaign targeting customers utilizing Barracuda’s Email Security Gateway to hackers
Goodbye, Tina Turner
Sad news this week that the Queen of Rock ‘n’ Roll has exited the stage. Many of us at the Randtronics team grew up hearing
Don’t take an Uber to the Big House
In a groundbreaking development, the ex-security chief of Uber has been convicted for his failure to disclose a significant data breach that occurred at the
Our Customers









